
Our penetration testing service is designed to enhance the security of our clients' applications, systems, and business processes.
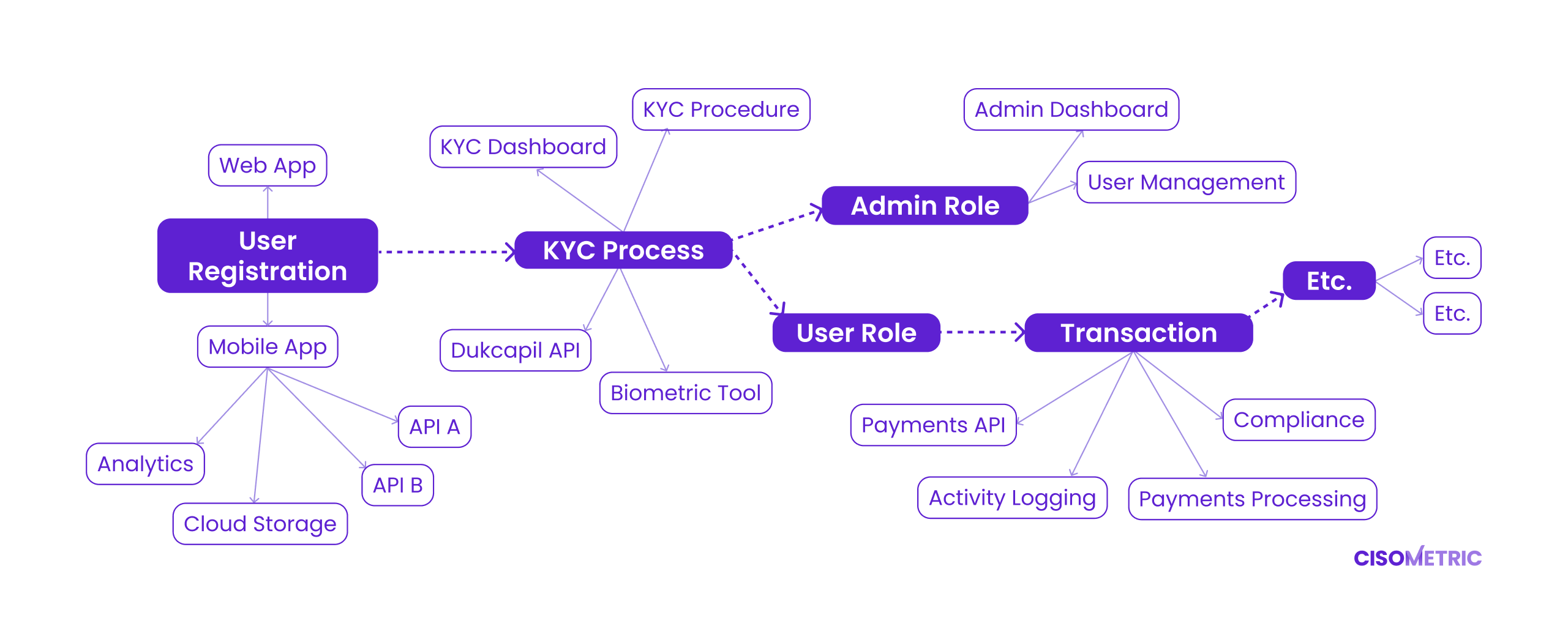
Our approach extends beyond a purely technical product perspective by also incorporating a thorough assessment of business process flows. This ensures comprehensive testing and meticulous identification of risks.
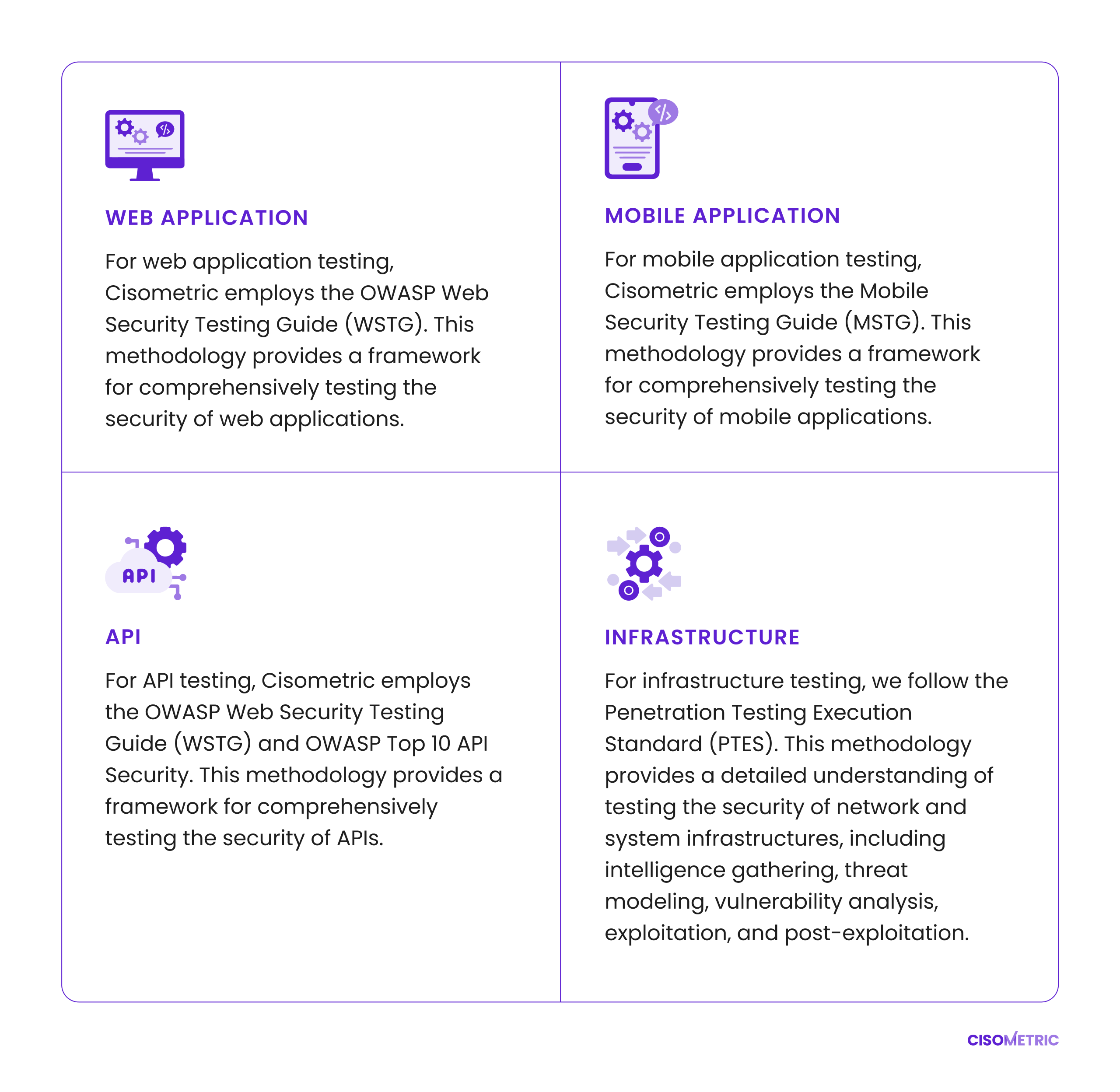
Our security testing approach extends beyond applications and systems to include a thorough analysis of business process flows. By examining interconnected services, processes, and human interactions, we identify risks that might otherwise go unnoticed. This comprehensive assessment ensures all potential vulnerabilities are recognized and mitigated.
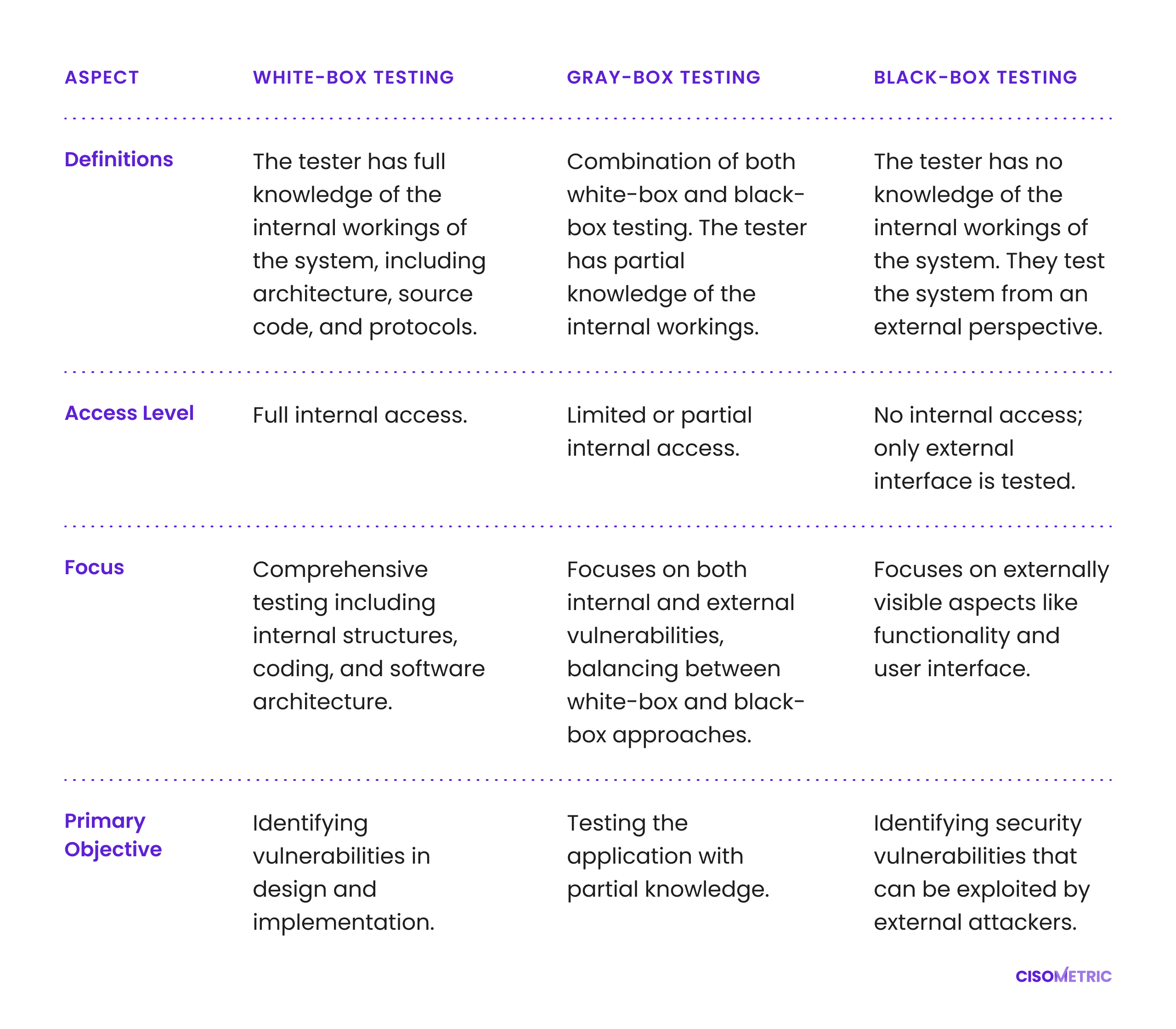
Our testing utilizes an approach that is mutually agreed upon with Xyz, tailored to meet specific project requirements. The table below details our methodology, which includes definitions, access levels, focal points, primary objectives, and its current applications.
The scope of Vulnerability Assessments and Penetration Testing engagements can vary depending on your application and business objectives.
Let’s define your requirements and get a custom quote!
